Proof-of-work scams have evolved beyond obvious fraud schemes to sophisticated attacks, including fake cloud mining operations with AI-generated deepfake CEOs, cryptojacking malware that silently drains device resources, and hardware pre-order scams using typosquatting domains. As cryptocurrency mining grows in 2026, these scams exploit technical complexity through 51% hashrate hijacking on smaller chains, fork claiming schemes that steal private keys, and malicious software distributed through fake trading bots.
Key Insights
- Proof-of-work scams now target miners and traders with advanced tactics that many fell for in the previous year.
- Some of these kinds of scams include fake mining, malware and fork traps that cause heavy losses each year
- As a prevention measure, simple checks help avoid most proof-of-work scams
Proof-of-work remains the backbone of major networks, including Bitcoin, Litecoin, and Dogecoin. Crypto has matured over the years, and as a result, scammers have refined their methods with smarter tactics.
Many of these attacks now hide deep inside mining and network mechanics, and proof-of-work scams no longer look as sloppy as they used to. Now, they appear polished and anyone can fall victim.
5 Most Common Proof-of-Work Scams in 2026
1. Fake Cloud Mining
Cloud mining once offered a real option for small investors. However, that era has faded, and proof-of-work scams now dominate this niche.
Scammers often start these attacks by building sleek websites. These sites show images of massive mining farms in locations like Iceland or Kazakhstan, where power is cheap.
They encourage buyers to purchase hash power contracts and promise steady daily payouts with fixed returns.

However, this detail alone reveals a big lie. Real mining income changes each day, depending on the network’s difficulty, the costs of power, and other factors.
Most of these platforms own no hardware and use funds from new users to pay earlier users in something very similar to a Ponzi scheme.
AI tools added a new wave between 2022 and the time of writing, with deepfake videos now showing fake CEOs touring facilities. These clips often come from Bitmain or Riot Platforms’ footage, and while the voices and faces look real, the farms do not exist.
2. Hashrate Hijacking
Bitcoin naturally resists direct network attacks because of its size. However, smaller proof-of-work chains are still exposed. Scammers launch new PoW coins and claim that they have improved speed or lower fees. Exchanges even list these assets after brief reviews sometimes.
However, these attackers quietly rent or deploy enough hash power to control more than 50%, and that control allows them to rewrite the entire chain.
Funds get deposited on exchanges, and coins sell for Bitcoin. The attacker then rewinds the chain, and the original deposit disappears.
3. Hardware Pre-Order Scams
Demand for mining hardware like ASICs and others tends to spike whenever new models appear. Proof-of-work scams thrive during these moments.
Fake resellers often create clone websites where names resemble real manufacturers like Bitmain, MicroBT or Canaan. They then make offerings and even discounts on their official sites.
These discounts attract buyers, and payment requests arrive in Bitcoin or USDT with a no refund policy.
Losses from this class of scams reached hundreds of millions during 2025, and attackers tend to use Typosquatting, where “Bitmain” can be written as “Bitmaiin” or “Bittmain”.
Scammers also sometimes ship fake tracking numbers, while others send empty boxes or bricks instead of proper mining rigs.
4. Cryptojacking Drains Devices Without Warning
Not all proof-of-work scams ask for money up front. Some steal resources silently.
In cryptojacking scams, attackers install hidden mining software in victims’ devices through fake trading bots or cracked software. Malicious ads are also used to spread these scripts.
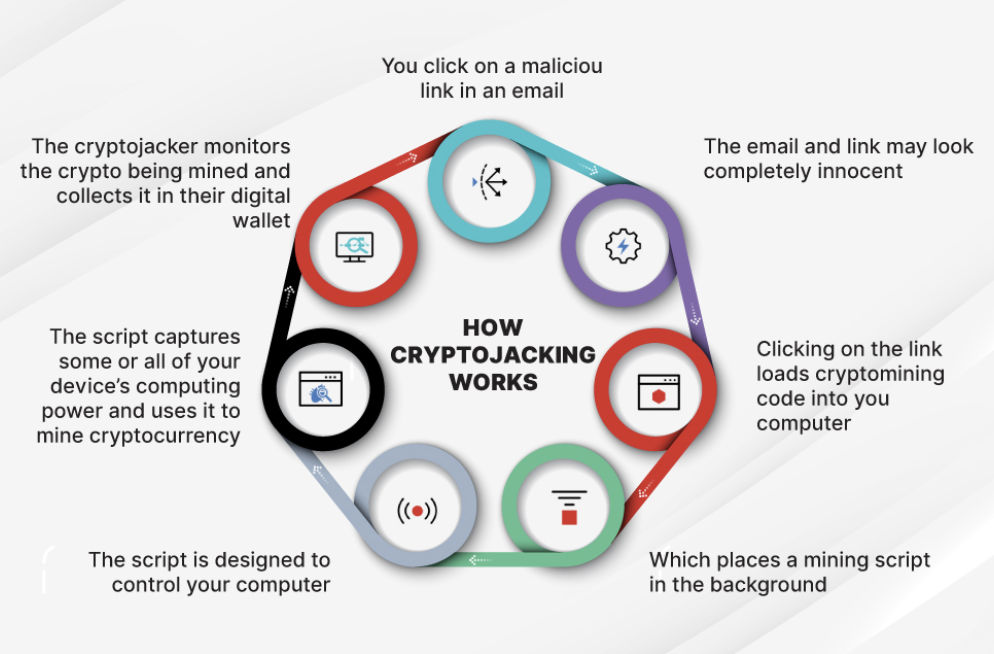
Once active, the software mines coins like Monero and sends them to the attacker’s wallet. On the user’s divide, CPU or GPU usage spikes and their systems slow down fast.
Their electric bills also rise, and the hardware ages faster. Reports show that this scam type was fairly common in 2025, before attackers moved toward cloud servers and enterprise systems instead of personal computers.
5. Fork Claiming Scams Exploit Confusion
Hard forks create confusion, even among experienced users, and proof-of-work scams can sometimes exploit this chaos.
Scammers announce fake forks with names resembling known brands. They even promise free coins based on past holdings.
They send users instructions to “claim assets” via websites that ask for seed phrases or private keys.
With this being said, real forks never require private keys, as wallet software can handle claims safely.
Disclaimer: This article is intended solely for informational purposes and should not be construed as financial advice. Investing in cryptocurrencies involves substantial risk, including the possible loss of your capital. Readers are encouraged to perform their own research and seek guidance from a licensed financial advisor before making any investment decisions. Voice of Crypto does not endorse or promote any specific cryptocurrency, investment product, or trading strategy mentioned in this article.









